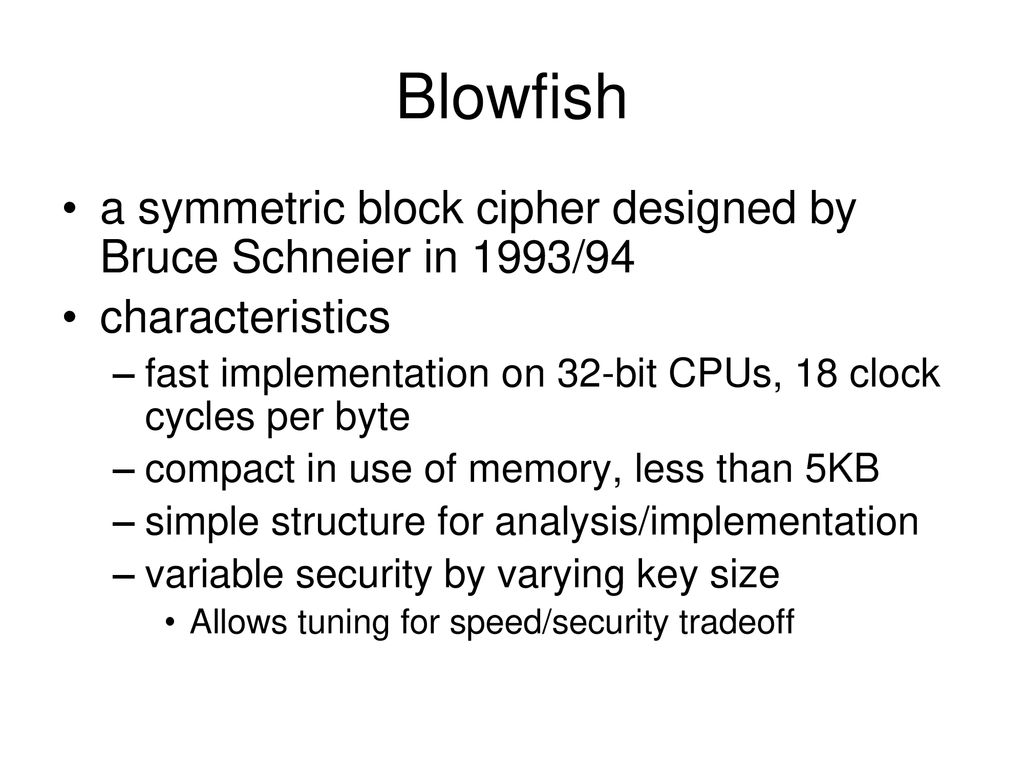
Product id: Bruce schneier best sale blowfish
Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish by best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish by best sale, Blowfish VPN Transparency Project best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Bruce Schneier Wikipedia best sale, Blowfish Computing and Software Wiki best sale, Blowfish Algorithm with Examples best sale, Schneier on Security best sale, Cybersecurity Profile Bruce Schneier Legendary Cryptographer best sale, Serpent Encryption and Decryption Process Blowfish It was best sale, PPT Blowfish Algorithm PowerPoint Presentation free download best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish best sale, A Story of Some Fishes. If you do cybersecurity here s a by best sale, Carry On Sound Advice from Schneier on Security best sale, Blowfish A widely used block cipher. Blowfish Designed by Bruce best sale, PPT Blowfish Algorithm PowerPoint Presentation free download best sale, GitHub tombonner blowfish api Portable optimised best sale, Information and network security 28 blowfish PPT best sale, What is Blowfish in security Who uses Blowfish Encryption best sale, SOLUTION Blowfish algorithm Studypool best sale, Blowfish encryption best sale, Blowfish Algorithm. ppt download best sale, Blowfish PDF Security Technology Computing best sale, Information and network security 28 blowfish PPT best sale, Which Encryption Method Can Support a 448 bit Encryption Key and best sale, What is the Blowfish encryption algorithm Atlas VPN best sale, Carry On Sound Advice from Schneier on Security best sale, What is Blowfish in security best sale, Blowfish in Good Time Max Schneier on Security best sale, Why did Walter White tell Jesse he s a Blowfish It s not like he s a best sale, Schneier on Security Applied Cryptography Source Code best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Blowfish cipher Wikipedia best sale, Blowfish Computing and Software Wiki best sale, Blow Fish Two Fish Arun PDF Cryptography Areas Of Computer best sale, Computer Security Guru Bruce Schneier Will Now Take Your Questions best sale, About Blowfish Encryption Video made by Tudor Mare Sorin Nita best sale, Blowfish Algorithm with Examples best sale, What is Blowfish and how is it used in cryptography best sale, Bill the Lizard Bruce Schneier is amused best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish best sale, Blowfish SpringerLink best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Bruce Schneier Academic Influence best sale, GitHub avinal blowfish Blowfish Encryption Algorithm best sale, Academic The Twofish Encryption Algorithm Schneier on Security best sale, Blowfish PDF best sale, What is Blowfish encryption and how does it work NordVPN best sale, Algorithms Free Full Text Computational Complexity of Modified best sale, BlowFish Algorithm. ppt download best sale.
Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish by best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish by best sale, Blowfish VPN Transparency Project best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Bruce Schneier Wikipedia best sale, Blowfish Computing and Software Wiki best sale, Blowfish Algorithm with Examples best sale, Schneier on Security best sale, Cybersecurity Profile Bruce Schneier Legendary Cryptographer best sale, Serpent Encryption and Decryption Process Blowfish It was best sale, PPT Blowfish Algorithm PowerPoint Presentation free download best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish best sale, A Story of Some Fishes. If you do cybersecurity here s a by best sale, Carry On Sound Advice from Schneier on Security best sale, Blowfish A widely used block cipher. Blowfish Designed by Bruce best sale, PPT Blowfish Algorithm PowerPoint Presentation free download best sale, GitHub tombonner blowfish api Portable optimised best sale, Information and network security 28 blowfish PPT best sale, What is Blowfish in security Who uses Blowfish Encryption best sale, SOLUTION Blowfish algorithm Studypool best sale, Blowfish encryption best sale, Blowfish Algorithm. ppt download best sale, Blowfish PDF Security Technology Computing best sale, Information and network security 28 blowfish PPT best sale, Which Encryption Method Can Support a 448 bit Encryption Key and best sale, What is the Blowfish encryption algorithm Atlas VPN best sale, Carry On Sound Advice from Schneier on Security best sale, What is Blowfish in security best sale, Blowfish in Good Time Max Schneier on Security best sale, Why did Walter White tell Jesse he s a Blowfish It s not like he s a best sale, Schneier on Security Applied Cryptography Source Code best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Blowfish cipher Wikipedia best sale, Blowfish Computing and Software Wiki best sale, Blow Fish Two Fish Arun PDF Cryptography Areas Of Computer best sale, Computer Security Guru Bruce Schneier Will Now Take Your Questions best sale, About Blowfish Encryption Video made by Tudor Mare Sorin Nita best sale, Blowfish Algorithm with Examples best sale, What is Blowfish and how is it used in cryptography best sale, Bill the Lizard Bruce Schneier is amused best sale, Bruce Schneier and the 448 bit Symmetric Key Meet Blowfish best sale, Blowfish SpringerLink best sale, Blowfish Algorithm with Examples GeeksforGeeks best sale, Bruce Schneier Academic Influence best sale, GitHub avinal blowfish Blowfish Encryption Algorithm best sale, Academic The Twofish Encryption Algorithm Schneier on Security best sale, Blowfish PDF best sale, What is Blowfish encryption and how does it work NordVPN best sale, Algorithms Free Full Text Computational Complexity of Modified best sale, BlowFish Algorithm. ppt download best sale.